Visibility and control
over your sensitive data
Precisely track and secure high-risk files
Sensitive data is hiding in all kinds of files. Any lack of awareness regarding sensitive data can result in significant issues or even disasters.
A powerful platform trusted by uncompromising organizations
Clients





Partners





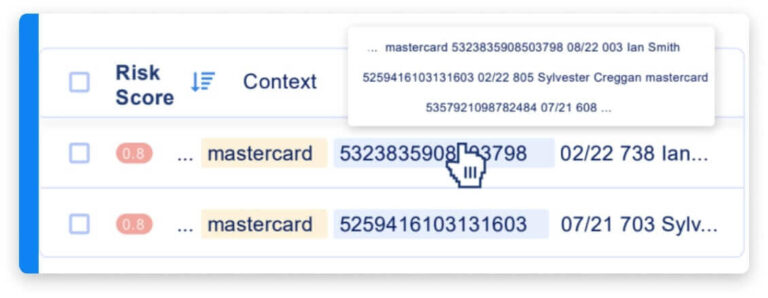
From initial inventory to remediation
Qohash's Qostodian
platform scans
You hate wasting time.
You’ll love us.
Rapid, organization-wide deployment within days, delivering precise tracking of sensitive data such as social security numbers across files and sources. Our pricing is flat-rated for a transparent, predictable cost structure.
Quick deployment
Organization-wide deployment within days
Granular data tracking
Unique data element tracking technology
Predictable flat-rate pricing
Transparent all-included cost model
Solutions By Role
Information security leader
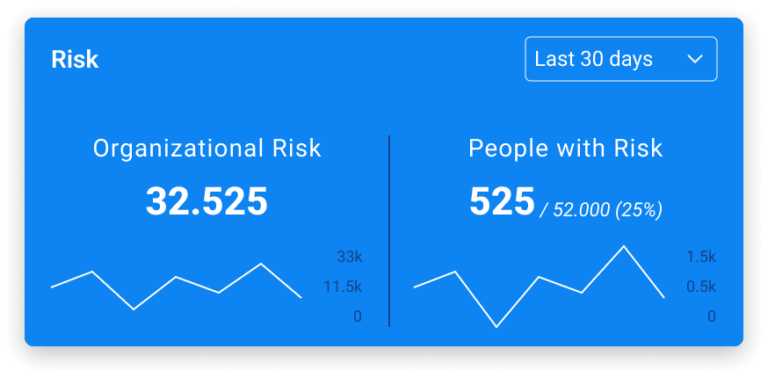
- Monitor user behavior and stay ahead of incidents.
- Watch risky employees. Quantify behavioral risk, and take action to establish needed controls.
Security analyst
- Save time with automated views and threat prioritization.
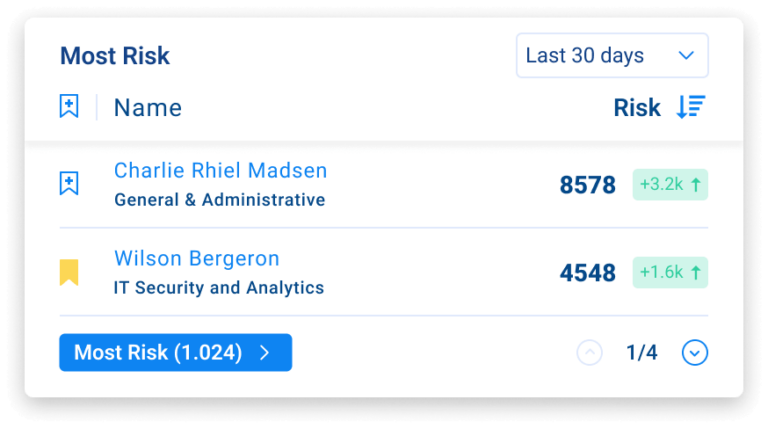
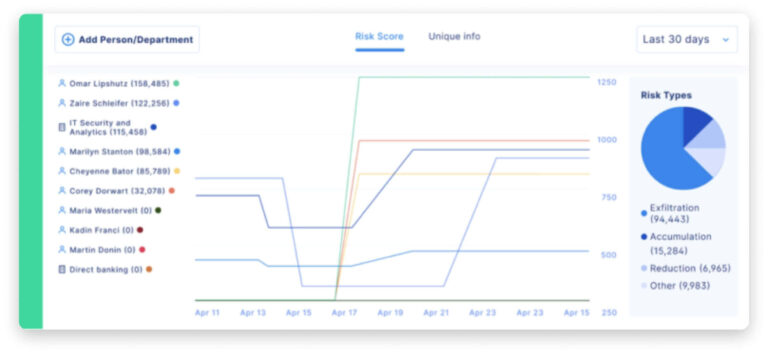
- Risk is surgically ranked, contextualized and prioritized. Granular views of specific data elements enable reverse search to see every employee and location data touched.
Compliance officer
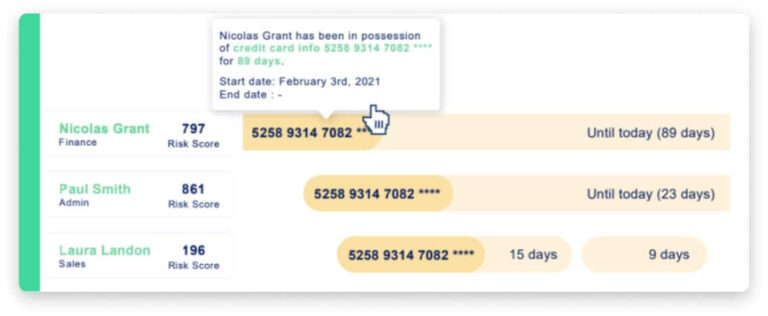
- Find sensitive data anywhere, 50x faster.
- Lightning-fast Qostodian provides a complete inventory of sensitive, unstructured data at rest.
Why customers are making the switch to Qohash
3 months saved
5-min implementation
20x faster investigations
20 hours of investigation
Automated reverse search
Answers 10x faster
10 GB/hour
$$$ saved
3 servers and 5 administrators
1 virtual machine
Recon enables us to cut through the noise, weed out false positives and focus on what matters. It helped us drive the success of the data governance and cloud migration projects. It also helped reduce costs by ensuring only necessary data made it into the cloud.

Claire Rosati
Associate Director, Project & Portfolio Office, Niagara College

We now manage sensitive data more effectively. We monitor risky employees and receive real-time, actionable alerts when non-compliant behavior occurs. We also automatically see how data moved across employees.

Frederic Michaud
Principal Director, Evolution of Cybersecurity Threats, Desjardins

I needed facts in the form of a comprehensive data inventory. In this job, you never want to go on assumptions. MNP recommended Recon because it gives us a full picture of all sensitive customer data in our possession – on servers, cloud drives, emails and even laptops.

Olivier Beauregard
Director of Internal Audits, Energir

We switched to Qohash because it was faster and lighter than our legacy solution. We installed it in minutes (rather than months). It requires less time and money to maintain, and yet delivers business-critical answers 10x faster. It’s been a game-changer for us at CAA.

George Plytas
Head of Information Security, CAA Club Group

What sold me on Recon is that it has the lightest footprint, while also delivering the most granular scanning results. The context provided gives the results meaning, and enables me to move quickly and confidently to secure sensitive data.

Ramadji Doumnande
Director of IT Operations and Security, NPCA

Recon helped us adapt to new regulatory requirements. We now quickly generate an audit-ready report to provide to regulators. We can also provide evidence that data was ‘destroyed.’ Best of all, our customers’ data is anonymized and never leaves our environment.

François Lamontagne
Director of IT, Kaleido







